Protect Your Business with DDoS Protected Dedicated Servers
Soraxus Assistant
January 17, 2026 • 21 min read

Think of a DDoS protected dedicated server as a fortress. It gives you all the power and exclusive resources of a high-end server, but it's also wrapped in a sophisticated security system built specifically to deflect malicious traffic. This setup is the bedrock for any online business that can't afford to go down.
Why Protected Servers Are No Longer Optional
Imagine your website is a bustling downtown storefront. A standard dedicated server is like leasing a fantastic building in a prime location, but you have no security guard. A DDoS attack is the digital equivalent of an angry mob swarming your entrance, deliberately blocking the doors so legitimate customers can't get in. Your store is still technically open, but for all practical purposes, it's out of business.
That's exactly what an unprotected server faces. Attackers overwhelm it with a tidal wave of junk traffic, maxing out its network pipe, CPU, and memory. Your actual users are met with connection timeouts and error pages, which translates directly to lost sales and a tarnished reputation.
A DDoS protected dedicated server is that expert security team standing guard. It intelligently spots and filters out the hostile traffic long before it ever gets near your front door, making sure it’s business as usual for your customers.
It's Not Just About Raw Power
Many people think that a beast of a server with tons of processing power can simply muscle through heavy traffic. But a DDoS attack isn't just "heavy traffic"—it's a targeted, weaponized flood designed to break things. Even the most powerful server in the world will be brought to its knees if its internet connection is completely saturated.
A practical example of this is a powerful gaming server. You might have the latest 16-core CPU and 128GB of RAM, but if an attacker sends a 100 Gbps flood of junk traffic and your server's internet connection is only 10 Gbps, your hardware's power becomes irrelevant. The connection is completely clogged, and no player data can get in or out.
This is where specialized protection proves its worth. The game isn't won with a faster server, but with a smarter, more resilient network infrastructure defending it. Without that defensive layer, your investment in top-tier hardware is left totally exposed.
A server's impressive specs mean nothing if its network connection is choked off. Effective DDoS protection ensures your hardware's resources are always reserved for genuine users, protecting both your uptime and your investment.
Who's in the Crosshairs?
The hard truth is that any online service can be a target. The list is long: competitive gaming servers, high-stakes e-commerce stores, and mission-critical SaaS platforms are all prime targets. The motives range from crippling a competitor to extortion or even just random cyber-vandalism.
The results, however, are always the same: costly downtime. For any business where uptime is tied directly to revenue and brand trust, running on unprotected infrastructure is a gamble you can't afford to take. You can see how modern DDoS protection services build a comprehensive shield around these critical digital assets.
How Modern DDoS Mitigation Actually Works
To really get why a DDoS-protected dedicated server is such a critical piece of infrastructure, you need to look under the hood at how the defense actually works. It's not just a simple firewall. Think of it as an incredibly smart, multi-layered security checkpoint that inspects every last bit of data heading your way. The goal isn't just to block traffic, but to surgically identify an attack's specific signature and neutralize it without harming legitimate users.
The First Line of Defense: Layers 3 & 4
The action starts right at the edge of the network, where the most common, brute-force attacks happen. We're talking about Layer 3 (Network) and Layer 4 (Transport) attacks.
A classic example is a SYN flood. Imagine your server's reception desk gets flooded with thousands of phone calls. The receptionist answers each one, says "Hello, please hold," and waits for a response that never comes. Very quickly, every single phone line is tied up, and genuine callers just get a busy signal. That's exactly how a SYN flood overwhelms a server's connection capacity, bringing it to a grinding halt.
To stop this, a good mitigation system uses a couple of key tactics:
- Rate Limiting: This is like giving the receptionist an automated switchboard. If thousands of calls suddenly come from the same number, the system automatically drops all but the first few. This prevents the lines from being tied up by a single bad actor.
- IP Filtering & Reputation Analysis: The system keeps a running list of known trouble-makers. When a call comes in from a number on that blocklist, it's instantly disconnected before it even has a chance to ring.
This is what that protection looks like in practice—a shield that actively filters out the bad traffic before it ever gets a chance to knock on your server's door.
As you can see, it’s an active barrier, not a passive wall. It’s designed to let your real customers through while keeping the angry mob of malicious traffic out.
Fending Off the Smart Attacks: Layer 7
Handling the brute-force floods is one thing, but the really tricky threats operate at Layer 7 (Application). These attacks are far more subtle and are designed to drain your server's brainpower—its CPU and RAM.
Instead of flooding the phone lines, imagine an attacker sends thousands of legitimate-looking requests for a super complex report that requires your top analyst to spend hours compiling data. Each request looks innocent on its own, but when they come in by the thousands, your entire expert team is tied up on these fake tasks, with no time left for actual work. This is how Layer 7 attacks, like HTTP floods, exhaust a server’s processing resources.
Defending against these requires a much smarter, more adaptive approach:
- Behavioral Analysis: The system first learns what "normal" activity looks like on your server. When it suddenly sees a massive spike in requests for a resource-heavy search query that nobody ever uses, it immediately flags that traffic as suspicious.
- Intelligent Challenges: For traffic that seems fishy, the system can issue a quick test, like a CAPTCHA or a JavaScript challenge. A real human won't have a problem with it, but the automated bots behind the attack will fail instantly. Once they fail, they're blocked.
Layer 7 protection is the difference between a bouncer at the door and a detective inside the party. The bouncer stops the obvious troublemakers, but the detective identifies the well-disguised spies who are already mingling with the guests.
The Global Shield: Scrubbing Centers
So what happens when an attack is just too massive for any single checkpoint to handle? Some volumetric attacks can top hundreds of gigabits—or even terabits—per second. That’s enough to overwhelm an entire data center's internet connection. This is where a global network of scrubbing centers comes in.
Think of scrubbing centers as a network of massive, regional water purification plants. When a tidal wave of polluted water (the DDoS attack) is headed for your town (your server), it doesn't go there directly. Instead, all traffic is rerouted to the nearest purification plant.
Inside that facility, specialized hardware "scrubs" the traffic, separating the malicious attack packets from the clean, legitimate user requests. Only the good traffic is then forwarded to your server over a secure, private link.
By distributing this filtering job across a global network, even the biggest attacks imaginable are absorbed and neutralized far away from your infrastructure. Your server never even feels the brunt of the storm. This distributed defense is what makes a truly resilient DDoS-protected dedicated server solution possible.
Key Security Metrics You Can't Afford to Ignore
When you're shopping for a DDoS-protected dedicated server, it's easy to get lost in marketing buzzwords. But the truth is, not all protection is created equal. To find a solution that will actually keep you online when an attack hits, you need to dig into the numbers—the real-world metrics that define a provider's defensive capabilities.
These figures aren't just specs on a page; they're the difference between seamless uptime and a catastrophic outage. Let's break down what you absolutely need to look for.
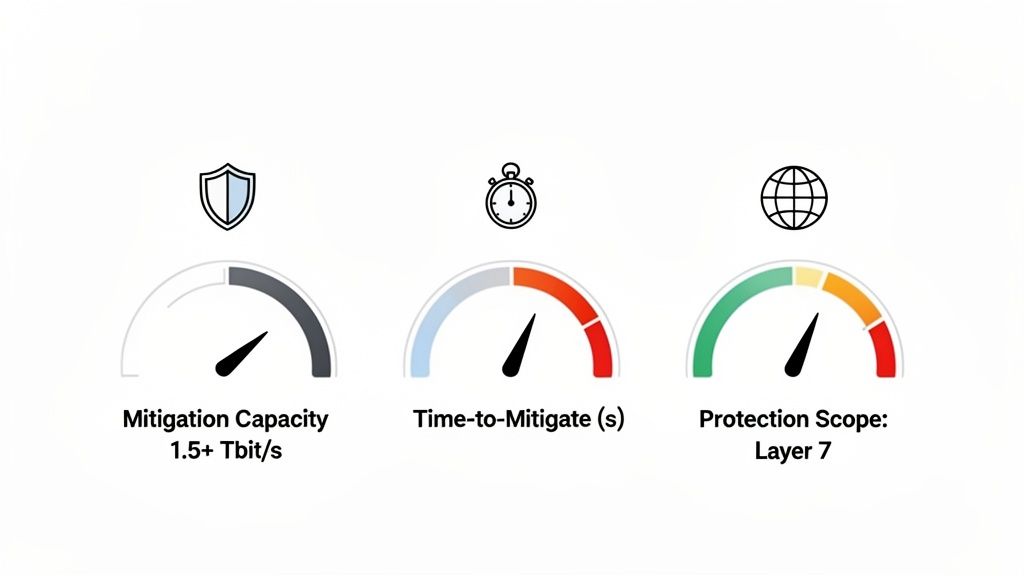
Mitigation Capacity (Tbit/s)
Think of mitigation capacity as the raw, brute-force strength of a provider's defense network. Measured in terabits per second (Tbit/s), it's the absolute maximum volume of malicious traffic the system can absorb and clean at any given moment. Imagine it's a dam holding back a flood—a small dam will be overwhelmed quickly, while a massive one can withstand a historic storm.
With modern attacks regularly smashing past hundreds of gigabits per second, a provider with a small, under-provisioned network is a huge liability. One big attack could easily overwhelm their entire system, taking you (and all their other clients) down with it.
For any serious online project, you should consider a global mitigation capacity of 1.5 Tbit/s the absolute minimum. Anything less is just not equipped to handle the scale of today's volumetric attacks.
Time-to-Mitigate (TTM)
Time-to-Mitigate (TTM) is all about speed. It measures how quickly the protection system can spot an incoming attack and swing into action to start filtering it out. This is measured in seconds, and every single second counts.
A delay of even 30 seconds can be enough to overload a server and knock your application offline. For businesses where every moment of uptime matters, a slow response is a deal-breaker.
Practical Example: The Cost of a Slow Response Let's say you run an e-commerce site during a flash sale. An attack starts, but it takes your provider 45 seconds to react. In that short window, your site is unresponsive. Carts are abandoned, frustrated customers leave, and the momentum of your sale is completely lost. That brief outage could cost you thousands in revenue and damage your brand's reputation—all because the TTM was too long.
This is why an "always-on" solution with sub-second detection is so critical for a DDoS protected dedicated server. Protection should be instant, leaving no gap for an attack to slip through and cause damage.
Protection Scope (Layers 3-7)
Protection scope tells you what kind of attacks the service can handle. A lot of basic, budget-friendly providers only cover Layers 3 and 4 (the network and transport layers). This is fine for stopping simple volumetric floods, but it leaves your application wide open to more sophisticated attacks.
A comprehensive solution needs to protect the full stack:
- Layers 3/4: This is your defense against brute-force volumetric attacks like SYN floods and UDP amplification, which try to clog your network pipe.
- Layer 7: This is where advanced attacks like HTTP floods happen. These are sneakier, targeting your server's application resources (like CPU and RAM) to bring it down.
Only having Layer 3/4 protection is like locking your front door but leaving all the ground-floor windows open. You need to confirm that any provider has robust, detailed plans for mitigating Layer 7 attacks, as this is where many cheap solutions fail.
The Service Level Agreement (SLA)
Finally, the Service Level Agreement (SLA) is where a provider puts their money where their mouth is. It’s a binding contract that guarantees a specific level of performance and uptime. A strong SLA is your assurance that the provider is confident enough in their tech to face financial penalties if they don't deliver.
You should be looking for an SLA that promises at least 99.99% uptime. That translates to less than one hour of potential downtime over an entire year. A good SLA will clearly define what’s covered, the compensation you’ll receive if they fail, and how to make a claim. It's the ultimate litmus test of a provider's reliability.
DDoS Protection Metrics At a Glance
Here’s a quick-reference table to help you compare providers and ensure you're asking the right questions.
| Metric | What It Measures | Why It Matters | Ideal Benchmark |
|---|---|---|---|
| Mitigation Capacity | The total volume of attack traffic the network can handle (Tbit/s). | Prevents the defense system from being overwhelmed by large attacks. | 1.5+ Tbit/s |
| Time-to-Mitigate | How quickly the system detects and starts filtering an attack (seconds). | Minimizes service disruption; a slow response can still lead to an outage. | Under 1 second (Always-on) |
| Protection Scope | The types of attacks covered, from Layer 3 (network) to Layer 7 (application). | Protects against both simple volumetric floods and complex application attacks. | Full L3–L7 Coverage |
| Uptime SLA | The provider's contractual guarantee for service availability. | Provides financial recourse if the provider fails to meet their promise. | 99.99% or higher |
Keeping these four critical metrics in mind will empower you to cut through the marketing fluff and choose a DDoS protection solution that genuinely has the power, speed, and scope to defend your server.
Who Needs a Protected Server the Most?
Let's be honest—anyone with a website can be hit by a DDoS attack. But for some, it's not just an annoyance. It's a full-blown crisis. In certain industries, uptime is the entire business model, and any disruption spells immediate disaster. For these high-stakes operations, a DDoS protected dedicated server isn't just a good idea; it's the bedrock of their survival.
These businesses don't just need powerful hardware. They need an ironclad guarantee of availability. A few minutes of downtime can trigger a domino effect of financial loss, shattered customer trust, and operational chaos. Let's look at the sectors where this level of protection is absolutely mandatory.
Online Gaming Communities
In the world of online gaming, lag is the ultimate villain and uptime is king. Gamers pour their time and passion into competitive matches, and the entire experience depends on a server that's fast and stable. Even a split-second of lag or a dropped connection during a key moment can cost someone the game, infuriate players, and send them packing to a competitor.
Attackers know this is a weak spot. A rival group or even a single disgruntled player can rent a cheap DDoS attack and bring a server to its knees, ruining the fun for thousands. This is why any serious game server host needs always-on, low-latency DDoS protection. The mitigation has to be instant, scrubbing out bad traffic without adding any perceptible delay for legitimate players.
- What's at risk: Player loyalty, community reputation, and in-game purchases.
- Protection priority: Instant, invisible attack filtering that doesn't compromise the gaming experience.
SaaS and E-commerce Platforms
For Software-as-a-Service (SaaS) and e-commerce companies, their platform is their business. If a SaaS application is offline, the company effectively has its "out of office" sign on. For an online store, every minute of downtime means abandoned shopping carts and lost sales—sometimes thousands of dollars' worth.
Think about a popular e-commerce site during a Black Friday sale or a B2B SaaS platform that runs a client's entire workflow. An attack that knocks them offline for just 15 minutes can cause massive financial damage and do lasting harm to their reputation. Customers expect these services to be available 24/7. A DDoS protected dedicated server is how you deliver on that promise.
For any business where availability is directly linked to revenue and customer data, even a small service disruption is a major emergency. Consistent, multi-layered protection is the only way to keep things running and hold onto customer trust.
Enterprises with Critical Infrastructure
Big companies rely on a complex web of internal systems to function. We're talking about the heavy hitters: Enterprise Resource Planning (ERP) software that manages the supply chain, or the databases that hold all customer and financial data. These aren't just applications; they're the company's central nervous system. An attack that takes down this core infrastructure can grind a global operation to a halt.
Picture a manufacturing giant whose ERP system goes dark. Suddenly, the factory floor can't get production orders, warehouses can't track inventory, and trucks can't be scheduled for shipment. The chaos is immediate and costly. For these organizations, proactively protecting their servers is a core part of risk management. When the stakes are this high, many turn to outside experts to manage their infrastructure. You can learn more about this approach in our guide on managed service provider solutions.
The need for this protection is only growing. The global DDoS protection market was valued at USD 4,516.8 million in 2025 and is expected to surge to USD 10,959.4 million by 2032. This growth is fueled by massive attacks, some now topping 2 Tbps, making it clear that unprotected infrastructure is a gamble no serious business can afford to take. You can find more data on the growing DDoS protection market on coherentmarketinsights.com.
Choosing The Right Dedicated Server Provider
Picking a provider for DDoS-protected dedicated servers is about so much more than comparing a single mitigation number on a pricing page. You have to look at the whole picture—from the silicon running your code to the actual engineers who answer the phone when things go wrong. Getting it right means finding a true partner that can keep you online, fast, and secure.
Think of it as choosing a co-pilot for a critical mission. The right one keeps your application running smoothly, while the wrong one can leave you with laggy performance, confusing support calls, and, inevitably, expensive downtime.
Hardware and Network Foundations
Before you even get to the DDoS protection specs, you have to kick the tires on the core infrastructure. After all, the best mitigation shield in the world won’t do you any good if it's protecting a slow server or a congested network. Your application's performance starts right here.
Take a hard look at the hardware. A serious provider will offer the latest-gen CPUs from Intel and AMD, backed by screaming-fast Gen4 or Gen5 NVMe storage. For most modern applications, that combination is non-negotiable for delivering the low latency your users demand. The availability of high-performance bare metal servers is usually a dead giveaway that a provider cares about quality.
The network is just as crucial. You want a provider that runs its own globally optimized network with a diverse blend of Tier-1 carriers. This is how you ensure traffic takes the fastest, most direct route to your users, no matter where they are. Always ask about their network blend and bandwidth guarantees to avoid getting stuck in a digital traffic jam.
A Deeper Look at Mitigation and Support
Once you’ve confirmed the hardware and network are solid, it’s time to dig into the DDoS mitigation itself. A provider's global footprint is a huge deal here. A distributed network of scrubbing centers means attacks are intercepted and cleaned close to their source, which cuts down on latency and dramatically increases the total capacity to absorb a massive assault.
But the technology is only one piece of the puzzle. The human element—the expert support team—is what separates a good provider from a great one.
Here’s a practical story: An e-commerce shop picks a budget host because the monthly price is low and the "Gbps protection" number looks big. Then, a sophisticated Layer 7 attack hits during their biggest holiday sale, and the site goes down. The provider's support team, trained only for basic tickets, has no idea how to stop an application-layer flood. Hours of downtime and thousands in lost revenue later, the business learns a tough lesson: expert support isn't an add-on; it's a core feature.
When you’re vetting support, ask some direct questions:
- Can I get in touch with actual network engineers 24/7, or am I stuck with a first-line call center?
- What’s your real-world average response time for a critical security event?
- Is your team able to help me write custom filtering rules for threats targeting my specific application?
Their answers will tell you if you're just buying a commodity server or investing in a fully-managed security solution. Real peace of mind comes from knowing that when an attack hits, there are genuine experts ready to jump in and help you fight back.
The Modern Threat Demands a Modern Defense
This level of scrutiny is essential because the threat landscape is evolving at a terrifying pace. DDoS attacks are no longer simple floods; they're complex, multi-vector nightmares. In the first half of 2025 alone, Layer 7 attacks skyrocketed by 38%, hitting over 563,000 incidents in Q2 and outnumbering Layer 3/4 attacks by 7.5 times.
One of these attacks peaked at a mind-boggling 859 million requests—a 270% increase from the previous quarter. To make matters worse, 52% of attacks now target multiple hosts at the same time, a tactic designed to bypass traditional, single-pipe defenses. This data, highlighted in a report on alarming DDoS trends on ddos-guard.net, makes it crystal clear: you need a provider with comprehensive, multi-layered protection and an expert-led, rapid-response strategy.
Frequently Asked Questions About DDoS Protection
When you start digging into DDoS protection, a lot of practical questions pop up. Choosing the right setup for your dedicated server really comes down to the details of how different solutions work. Let's walk through some of the most common questions we get.
Always-On vs On-Demand Protection
The biggest difference between always-on and on-demand protection is how fast it kicks in. Think of always-on protection as a permanent security guard at your front door—it's constantly filtering your traffic, so malicious packets are dropped the second they show up. There's literally zero delay between an attack starting and the mitigation beginning.
On-demand systems are more like a security guard on call. They only show up after the alarm has been triggered. This creates a dangerous gap, which can last anywhere from 30 seconds to several minutes, where your server is taking the full brunt of the attack. That brief "time-to-mitigate" is often all it takes to knock you offline, even if it's just for a minute.
For any serious application where every second of uptime matters, always-on protection is non-negotiable. That small window of vulnerability with on-demand systems is often enough to disrupt your service and lose customer trust.
Can I Add Protection To An Existing Server?
Yes, you can bolt on DDoS protection to a server you already have. This is usually done with a third-party service that uses something like GRE tunneling to reroute your traffic to their scrubbing center. After it's cleaned, the "good" traffic is sent back to your server.
While this works, it adds a layer of complexity and, more importantly, can add noticeable latency. For example, if your server is in New York but your third-party protection service routes traffic through their London scrubbing center, every legitimate user request now has to cross the Atlantic Ocean and back. This added round-trip time can make your website feel sluggish. An integrated solution, where the protection is built right into your hosting provider's network, is almost always the superior choice. It keeps latency at an absolute minimum because your traffic isn't being bounced all over the internet.
How Much Mitigation Capacity Do I Need?
This is a classic "it depends" question, and it really comes down to your risk profile. Attacks are getting bigger, but that doesn't mean every project needs terabit-level defense. You just need to match your protection to the kind of threats you're likely to face.
Here’s a practical way to think about it:
- Small Businesses & Startups: You're probably dealing with more common, smaller-scale attacks. A plan with a few dozen Gbps of protection is often more than enough.
- Gaming & E-commerce: These industries are much bigger targets. You should be looking for protection in the hundreds of Gbps range to fend off more serious, targeted campaigns.
- Enterprise & High-Risk Industries: For anyone where downtime is simply not an option, a global mitigation capacity of 1.5+ Tbit/s is the baseline. This ensures you're covered against the massive volumetric attacks we see today.
The key is to find that sweet spot—enough protection to keep you safe without paying for massive capacity you'll never actually need.
Ready to secure your infrastructure with a true enterprise-grade solution? Soraxus provides high-performance DDoS protected dedicated servers with 1.5+ Tbit/s always-on mitigation, a 99.99% uptime SLA, and 24/7 expert engineer support. Explore our dedicated server solutions.